Configure MacOS Platform SSO
What is MacOS Platform SSO
Section titled “What is MacOS Platform SSO”Platform single sign-on (SSO) is a replacement for binding to directory services. It builds on enterprise SSO capabilities so SSO extensions can also perform single sign-on for apps and websites. It integrates with macOS and doesn’t use JavaScript or render webpages for authentication.
The system stores the SSO tokens in the keychain and only shares them with the SSO extension. The SSO extension then uses the SSO tokens to authenticate the user to their on-premises apps and on websites as needed. If the SSO tokens are missing, expired, or more than four hours old, platform SSO attempts to refresh or retrieve new tokens from the IdP.
Platform SSO supports the following authentication methods with an identity provider (IdP):
-
Password and encrypted password The IdP uses the local account password and keeps it in sync, including password updates from the login window and screensaver unlock.
-
Password with WS-Trust A federated IdP, meaning an IdP that facilitates federated authentication across multiple security domains, can use the local account password for authentication.
-
User secure enclave key A secure enclave-backed key can authenticate with the IdP without a password and without changing the local account password.
-
SmartCard High-security customers can use a SmartCard to authenticate with the IdP. Platform SSO can create new local user accounts on demand at the login window using IdP credentials, and also integrate IdP group membership with macOS. You can use network accounts for authorization, and groups can also authorize network accounts.
Use Device Management to securely configure platform SSO, including device and user registration, configuring groups, and managing account permissions.
The system can also retrieve Kerberos ticket-granting tickets (TGTs), import them to a credential cache, and optionally share them with the Kerberos SSO extension.
I will describe the config for Secure Enclave Key and will add Password authentication at a later time.
Configure Platform SSO With Secure Enclave Key
Section titled “Configure Platform SSO With Secure Enclave Key”Prerequisites
- Devices must be macOS 13.0 and newer devices. –> For the best results upgrade to MacOS 14.x
-Microsoft Intune Company Portal app version 5.2404.0 and newer.
- Supported web browsers: Microsoft Edge Google ChromePlatform Safari
Create the Platform SSO policy
Section titled “Create the Platform SSO policy”Go to Intune portal – Devices – MacOS – Configuration profiles – Create – New Policy – Platform MacOS – Profile type Settings Catalog – Name your policy e.g. MacOS – Platform SSO – Select Add Settings – Expand Authentication – Select Extensible Single Sign On (SSO).
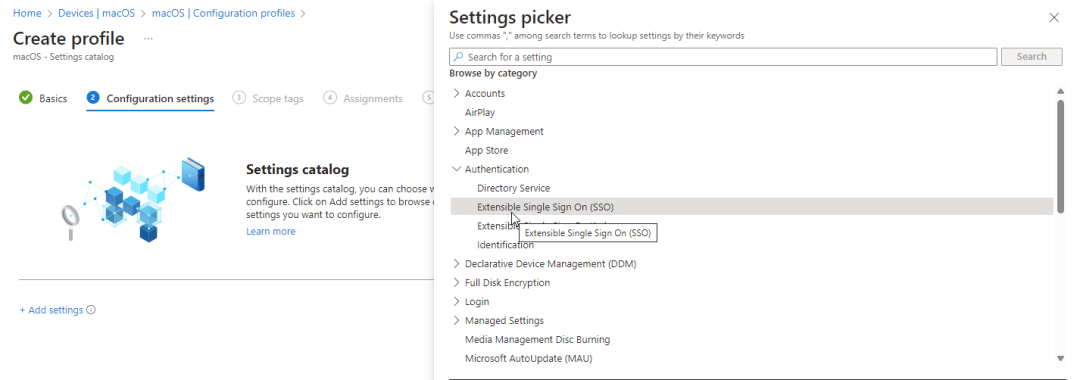
Configure the profile for at the below keys: (these are minimum required settings for PSSO to work)
-
Authentication Method (Deprecated) (only if you are deploying profile to macOS 13.x devices)
-
Extension Identifier
-
Authentication Method (macOS 14+)
-
Use Shared Device Keys
-
Registration Token
-
Account Display Name
-
Screen Locked Behavior
-
Team Identifier
-
Type
-
URLs
-
Token To User Mapping: Account Name
-
Token To User Mapping: Full Name
Here you can find all the info that you need to fill in: Configure Platform SSO for macOS devices | Microsoft Learn
As there is apparently some confusion on the use of the URL’s needed in the PSSO profile see here (although this is stated in de Microsoft docs – see link above) here just to clarify:
These URL prefixes are the identity providers that do SSO app extensions. The URLs are required for redirect payloads and are ignored for credential payloads.
If your environment needs to allow sovereign cloud domains, then also add the following URLs:
For more information on these URLs, go to Microsoft Enterprise SSO plug-in for Apple devices.
Your profile will look like this.
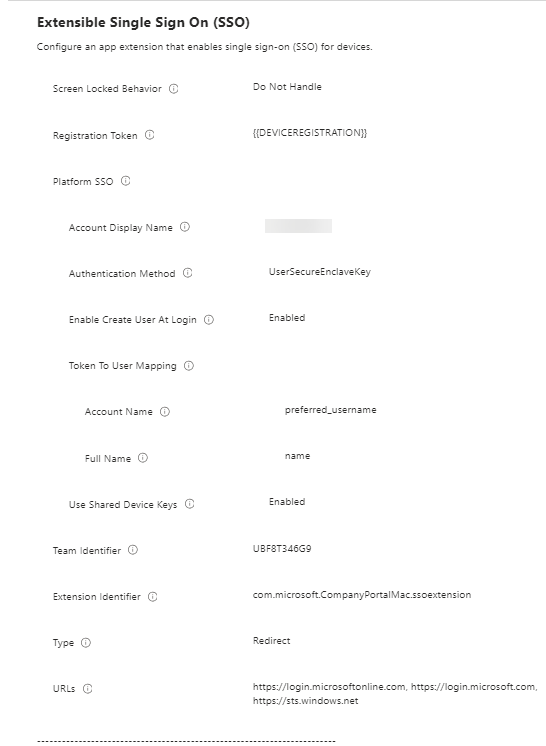
Assign the profile to your desired device or user group.
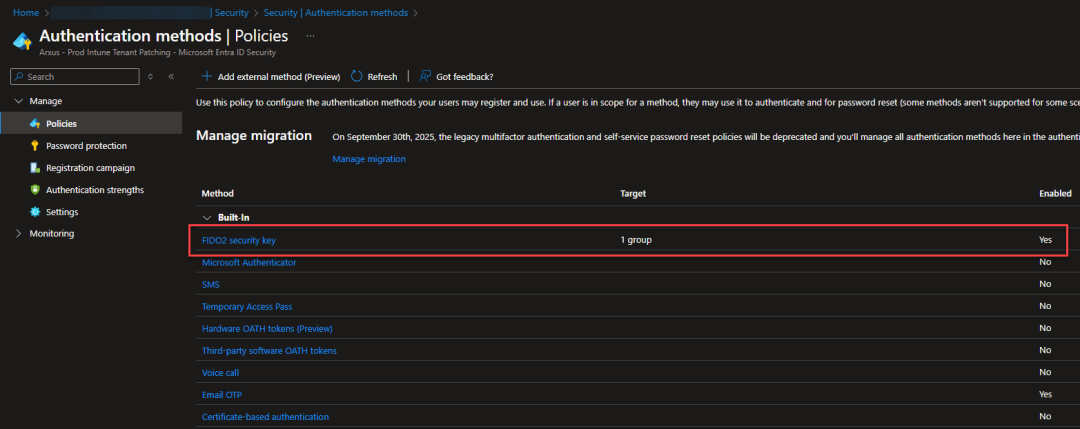
If you want to enable smart card login you will also need to enable FIDO as an authentication method in Entra ID:
title: Configure MacOS Platform SSO sidebar: order: 4
Section titled “title: Configure MacOS Platform SSO sidebar: order: 4”What is MacOS Platform SSO
Section titled “What is MacOS Platform SSO”Platform single sign-on (SSO) is a replacement for binding to directory services. It builds on enterprise SSO capabilities so SSO extensions can also perform single sign-on for apps and websites. It integrates with macOS and doesn’t use JavaScript or render webpages for authentication.
The system stores the SSO tokens in the keychain and only shares them with the SSO extension. The SSO extension then uses the SSO tokens to authenticate the user to their on-premises apps and on websites as needed. If the SSO tokens are missing, expired, or more than four hours old, platform SSO attempts to refresh or retrieve new tokens from the IdP.
Platform SSO supports the following authentication methods with an identity provider (IdP):
-
Password and encrypted password The IdP uses the local account password and keeps it in sync, including password updates from the login window and screensaver unlock.
-
Password with WS-Trust A federated IdP, meaning an IdP that facilitates federated authentication across multiple security domains, can use the local account password for authentication.
-
User secure enclave key A secure enclave-backed key can authenticate with the IdP without a password and without changing the local account password.
-
SmartCard High-security customers can use a SmartCard to authenticate with the IdP. Platform SSO can create new local user accounts on demand at the login window using IdP credentials, and also integrate IdP group membership with macOS. You can use network accounts for authorization, and groups can also authorize network accounts.
Use Device Management to securely configure platform SSO, including device and user registration, configuring groups, and managing account permissions.
The system can also retrieve Kerberos ticket-granting tickets (TGTs), import them to a credential cache, and optionally share them with the Kerberos SSO extension.
I will describe the config for Secure Enclave Key and will add Password authentication at a later time.
Configure Platform SSO With Secure Enclave Key
Section titled “Configure Platform SSO With Secure Enclave Key”Prerequisites
- Devices must be macOS 13.0 and newer devices. –> For the best results upgrade to MacOS 14.x
-Microsoft Intune Company Portal app version 5.2404.0 and newer.
- Supported web browsers: Microsoft Edge Google ChromePlatform Safari
Create the Platform SSO policy
Section titled “Create the Platform SSO policy”Go to Intune portal – Devices – MacOS – Configuration profiles – Create – New Policy – Platform MacOS – Profile type Settings Catalog – Name your policy e.g. MacOS – Platform SSO – Select Add Settings – Expand Authentication – Select Extensible Single Sign On (SSO).

Configure the profile for at the below keys: (these are minimum required settings for PSSO to work)
-
Authentication Method (Deprecated) (only if you are deploying profile to macOS 13.x devices)
-
Extension Identifier
-
Authentication Method (macOS 14+)
-
Use Shared Device Keys
-
Registration Token
-
Account Display Name
-
Screen Locked Behavior
-
Team Identifier
-
Type
-
URLs
-
Token To User Mapping: Account Name
-
Token To User Mapping: Full Name
Here you can find all the info that you need to fill in: Configure Platform SSO for macOS devices | Microsoft Learn
As there is apparently some confusion on the use of the URL’s needed in the PSSO profile see here (although this is stated in de Microsoft docs – see link above) here just to clarify:
These URL prefixes are the identity providers that do SSO app extensions. The URLs are required for redirect payloads and are ignored for credential payloads.
If your environment needs to allow sovereign cloud domains, then also add the following URLs:
For more information on these URLs, go to Microsoft Enterprise SSO plug-in for Apple devices.
Your profile will look like this.

Assign the profile to your desired device or user group.
If you want to enable smart card login you will also need to enable FIDO as an authentication method in Entra ID:
